How Do DMA Cards Work for Cheating?
DMA cards establish themselves as advanced tools that enable game hackers to bypass different anti-cheat protective measures. DMA cards function outside the system, which differs from conventional software cheats that modify files or insert code during process operation. The technology remains undetectable because of its difficult detection characteristics.
Players use hardware-based DMA cards to evade anti-cheat systems including BattlEye, EAC and Vanguard since these systems currently advance rapidly. These cheats remain undetectable because they read memory directly from a separate machine which offers data for ESP (wallhacks) and aimbots and other exploit functions.
What Are DMA Cards?
Direct Memory Access (DMA) functions within contemporary computers by letting specific hardware elements obtain system memory data through a direct connection that bypasses CPU involvement. Because of DMA's direct data transfer protocol, the system gains speed for multiple real-time computing activities, including video gaming and data processing and analysis.
The DMA card functions as a specialized external hardware device through PCIe or Thunderbolt/USB-C ports to perform memory data acquisition for computers. The external operation of DMA cards makes them undetectable to anti-cheat software because CPU involvement is not necessary as in traditional software methods.
Why Are DMA Cards Used?
· The Cybersecurity & Forensics field utilizes DMA cards for penetration tests and reverse engineering tasks as well as memory-dumping operations.
· DMA cards serve as a performance optimization tool because they increase computing speed and accelerate machine learning models.
· DMA cards enable players to detect game memory data in real-time without triggering any cheating alarms which enables them to implement ESP (wallhacks) and aimbots and extract game data.
How DMA Cheats Work in Games
DMA cards function within game hacking environments by obtaining live game data which consists of player positioning data alongside health indicators along with ammunition status and additional game variable details however this process does not alter game file contents. The operation of DMA cheats functions in the following sequence.
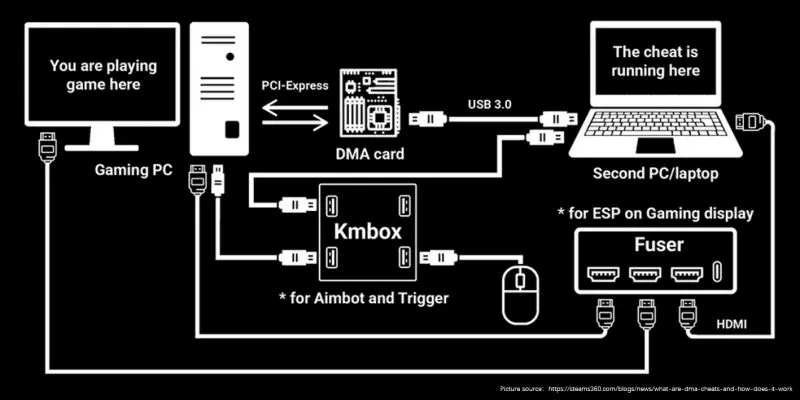
Step 1: Installing the DMA Card
Users can set up DMA cards through internal PCIe for installation or connect them externally through Thunderbolt/USB-C.
The user uses a second PC to process the extracted data after connecting the DMA card to it.
Step 2: Reading Game Memory
Through the DMA card users can bypass CPU security measures to obtain unprocessed memory data from gaming applications.
The data extraction process delivers information about player coordinates together with health points along with ammunition count and player motion data.
Step 3: Processing the Data
The data is transmitted to a different computer system using an external PC that executes a special program or runs machine learning capabilities.
The script cuts away unnecessary data while flagging down valuable details that include enemy position data.
Step 4: Displaying Cheat Information
The game screen displays the processed information through ESP (wallhack) functionalities that rely on separate displays or hardware components.
Alternatively, the received data enters an aimbot script that enables automatic enemy targeting.
DMA-based cheats remain highly effective since they exist outside the game environment, which allows them to avoid detection from anti-cheat software. Security teams against hackers engage in continuous battles because anti-cheat developers continuously develop methods to detect and defend against DMA exploitation.
Why Are DMA Cheats So Hard to Detect?
DMA cheats remain highly undetectable due to their hardware operation, which occurs beyond standard anti-cheat monitoring areas. External memory reading through DMA-based cheats eliminates any detectable modifications that happen when updating software program memory. There are multiple reasons why DMA cheats prove difficult for detection purposes.
1. No Direct Modification of Game Files or Memory
Anti-cheat programs BattleEye and EAC with Vanguard have enough power to find traditional cheats that use DLL injections or memory modifications. DMA-based cheats function through memory reading exclusively since this activity prevents them from altering the ongoing game process.
2. Operates outside the Game’s ecosystem
Players interface DMA cards through external hardware which connects using PCIe, Thunderbolt or USB-C ports thus leaving the game application unable to detect them. The scanning functionality of anti-cheat software is limited to internal memory processes so they cannot check what DMA cards extract from the system.
3. No DLL Injection or Process Modification
Game executables need modification or background third-party processes for the operation of traditional Aimbots ESP hacks and wallhacks. The memory-detection capability of DMA cheats functions without any code injections because it enables undetectability against signature-based detection methods.
4. DMA-activated cheats operate successfully over Networked Setups
DMA-based cheats available on the market offer network compatibility which enables game data extraction through a secondary PC linked by Wi-Fi or Ethernet connection. The physical separation of cheat operations from the gaming PC through this configuration makes it exceptionally difficult for anti-cheat software to spot any unusual behaviors.
Setting Up a DMA Card for Game Cheating
Establishing a DMA card setup for game cheats requires following particular configuration methods to operate without getting detected. Here’s a step-by-step guide:
1. Choosing the Right DMA Card
A variety of DMA cards exists within the market at present. Among game-cheating DMA products the most commonly used include Squirrel DMA and LeetDMA and PCILeech.
· Squirrel DMA – Known for its high-speed memory access.
· LeetDMA – A budget-friendly option with reliable performance.
· PCILeech stands out as a popular DMA attack tool that provides open-source support to users.
The latency speed mode differs by card along with its interface characteristics between PCIe and Thunderbolt and its anti-cheat bypass capabilities.
2. Setting Up the Software
The next stage involves configuring the software programs after obtaining the necessary hardware.
The connection between DMA card and FPGA drivers (Field-Programmable Gate Array) must be installed properly for communication to occur smoothly.
The system requires the programming of Python or C++ memory reading scripts that extract meaningful game parameters.
PCILeech and custom-built applications provide effective memory reading capabilities through their programming interface.
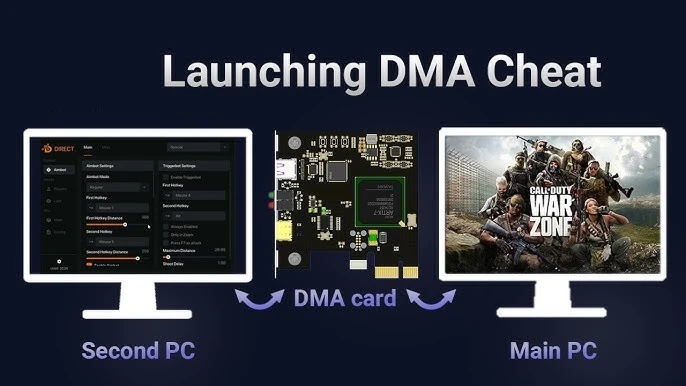
3. Connect an External PC for Safe Data Processing
The complete undetectability of hackers requires that they operate two personal computers where the first handles gaming activities while the second processes the extracted DMA data.
Through its software, the cheating PC translates memory values into enemy positions, which the gaming PC receives as game-related data.
The absence of monitoring activities on the gaming PC establishes impossible detection abilities because suspicious operations remain restricted to a different computer system.
4. Use a Spoofed MAC Address & VPN to Prevent Tracking
Using a DMA card without proper security measures still leaves you vulnerable to developer identification of your hardware, thus creating a risk of hardware-based banning.
A MAC address spoofer should always be used because it changes network adapter details.
Using a VPN or Proxy together with an IP address hiding tool will stop game developers from recognizing suspicious login activities.

Conclusion
DMA cards serve as a modern cheating device for video games which gives hackers outside access to external game memory while avoiding standard anti-cheat security. DMA exploit operations occur at the hardware level as opposed to software-based cheats leading to enhanced detection difficulty. DMA card benefits are limited by their high acquisition costs and installation intricacies and continual threat of game developer security enhancements.
DMA-based cheats serve as top-level undetectable methods during current times but their future existence remains doubtful. Research shows that AI-based anti-cheat security alongside enhanced hardware surveillance seems likely to eliminate the use of DMA cards. Cheat developers and security teams, currently play an ongoing detection game that might become more difficult for cheaters in an era of advanced technology.






0 Comments
Recommended Comments
There are no comments to display.